Saturday, February 24, 2007
Re-organize pictures in 3D
Computer scientists at the University of Washington and Microsoft are developing software for organizing digital photos. OK, nothing new. But overall, it can compile images from common scenes to create 3D virtual environments.
Photo Tourism could be used for creating virtual tours, recreating events or even developing a map from all the photos from the Internet.
"You might look at a photo and say I wonder what's just to the left of it, or I wonder what's just to the right of it, or I wish I could expand the field of view," says Noah Snavely, explaining the frustration when searching photo on classical tools as Flickr.
Photo Tourism examines details shared by images and can tell if they're representing the same scene. If yes, it fuses them together in a 3D model. For a better description of the software, please see the video and for a trial, there is a java applet here (chose live demo).
Photo Tourism could be used for creating virtual tours, recreating events or even developing a map from all the photos from the Internet.
"You might look at a photo and say I wonder what's just to the left of it, or I wonder what's just to the right of it, or I wish I could expand the field of view," says Noah Snavely, explaining the frustration when searching photo on classical tools as Flickr.
Photo Tourism examines details shared by images and can tell if they're representing the same scene. If yes, it fuses them together in a 3D model. For a better description of the software, please see the video and for a trial, there is a java applet here (chose live demo).
Source: UWnews.org, last week.
Labels: computers
Plants which find the anti-personnel land mines
 Danish biologists genetically modified a plant so it's able to detect the explosives hidden in the ground, and particularly the anti-personnel mines. The Arabidopsis thaliana has two different properties: the first is to be sensitive to nitrogen dioxide present in the explosives, the second is to produce anthocyanins, natural pigments that make the autumn's beautiful colours.
Danish biologists genetically modified a plant so it's able to detect the explosives hidden in the ground, and particularly the anti-personnel mines. The Arabidopsis thaliana has two different properties: the first is to be sensitive to nitrogen dioxide present in the explosives, the second is to produce anthocyanins, natural pigments that make the autumn's beautiful colours.The biologists shorted-circuit these two properties, creating a relation between the first and the second: when the Arabidopsis thaliana detects nitrogen dioxide, it produces the pigment and becomes red, whereas its classic maturation would like it green.
The idea is thus to sow the plant by helicopter and the result is visible after 3 to 6 weeks. Moreover, the researchers also made it sterile to avoid a proliferation which no one could control.
More than 100 million mines would be still hidden throughout the world in 75 countries, result of guerrillas and conflicts of any kind. Every twenty minutes, a person is mutilated or killed by a mine, and the majority of the victims are less than twenty years. Find and destriy the bombs is a slow and tiresome operation, which is carried out using dogs and machines.
Source: La question du jour on La Première, january the 5th
Labels: exploits
Saturday, February 17, 2007
Consume less fuel
 A University of Eindhoven researcher has teamed up with Ford to develop software that improves the fuel efficiency of automobiles. "By adding a piece of software and a simple cable, cars can save 2,6% of fuel consumption", explains the scientist John Kessel.
A University of Eindhoven researcher has teamed up with Ford to develop software that improves the fuel efficiency of automobiles. "By adding a piece of software and a simple cable, cars can save 2,6% of fuel consumption", explains the scientist John Kessel.This software simply switchs the battery-charging dynamo off when it is inefficient for the engine to power it, and back on when it is more efficient for the engine to
do so. Many hybrid vehicles already use this strategy.
All vehicles equipped with a engine computer can implement the solution. For Kessel, there are still concerns about the extent to which car batteries would be degraded by the software.
But what is 2,6% ? For you, it's about a few tens of dollars or euros. But for the planet ... a quick calculation ... the world consumes 80 millions barrels a year. At 159 litres by barrel, we get 13 billions liters of oil. If we remove the usage of kerozene or fuel oil, we can consider that the half leaves on the roads. And then 2,6% represents 170 millions of litres a year!
Source: NewScientistTech, last week.
Labels: ecology
GPS devices for speed camera warnings are banned from Switzerland
 According to the article 57b of the Swiss federal law last month, the PND with a speed camera warning function may not be bought, installed or put into vehicles, or even used in any manner.
According to the article 57b of the Swiss federal law last month, the PND with a speed camera warning function may not be bought, installed or put into vehicles, or even used in any manner.They may not be put on the market, i.e. fabricated, imported, sold or subjet of commercials.
According to the OFROU (Federal Road Office in Switzerland), police and customs may take those devices and establish a lawsuit. The tribunal will fix the fine and may judge the device's destruction. The OFROU has arguments and Tomtom politely answered. Yet, it advises the TomTom GO, RIDER, NAVIGATOR 6 and TomTom ONE users that have installed the Swiss Safety Camera Database to remove it when traveling in or through Switzerland.
Others involved devices are Garmin, Mio, Navman, Medion, Route66, Packard Bell, Sony and ViaMichelin ... at least.
Source: Engadget, beginning of the month.
For those who do not know: Some Portable Navigation Systems (PND) can warn you when you approach a fixed speed camera, if you installed a database provided by the manufacturer (Tomtom for example, the Safety Camera Database). This database can be updated day in day by using the police information or by the users via Internet or a mobile connection… Then you can download it regularly. If the process is fast enough, it's even possible to be aware of the position of the mobile cameras.
Labels: navigation
Saturday, February 10, 2007
Honesty on online dating sites

An american behavorial study concludes that 52.6% of men lied about their height, compared with 39% of women. But 64.1% of women did not tell the truth about their weight, compared with 60.5% of men. Also, 24.3 percent of men lied about their age, while 13.1 percent of women did.
According to an assistant who worked on the subject, participants try to find the good balance between 1) appearing as attractive as possible 2) being perceived as honest during thedeception first meeting.
Source: Cornell University, this monday.
According to an assistant who worked on the subject, participants try to find the good balance between 1) appearing as attractive as possible 2) being perceived as honest during the
Source: Cornell University, this monday.
Labels: anecdote
At work with my hacker
 Researchers of the University of Maryland enjoyed observing the activities of hackers as they try to gain access to a computer and exploit it. They set up 4 Linux computers, with an Internet connection and a weak security. These computers were attacked 2,244 times each day, i.e. every 39 seconds on average!
Researchers of the University of Maryland enjoyed observing the activities of hackers as they try to gain access to a computer and exploit it. They set up 4 Linux computers, with an Internet connection and a weak security. These computers were attacked 2,244 times each day, i.e. every 39 seconds on average!This is a very scary figure. A classic computer connected to the Internet is almost constantly under attack, more than two thousand times a day! This fact and the fact that 80% of animals on earth are insects, I'm not sure I can get sleep tonight...
Anyway. Most of these attacks employ automated scripts that indiscriminately seek out thousands of computers at a time, looking for vulnerabilities.
The study specifies the most commonly attempted user names: root, admin, test, guest, info, adm, mysql, user and administrator... Usernames to avoid! They are listed in dictionary scripts with others classical passwords: 123456, password, 1234, 12345, passwd, 123, test, 1 (!!) and more simply the repetition or a variation of the username, sometimes followed by 123. Scripts try and try, then sometimes it matches!
After gaining access, hackers would typically check the computer's software configuration, change the password, check the configuration again, and upload and install a program, a backdoor or a trojan that clean their passage and enable them to create a botnet and viva el spamos!
Source: PR Newswire, this tuesday.
For those who do not know:
- The botnet is a jargon term for a collection of software robots, or bots, which run autonomously. This can also refer to the network of computers using distributed computing software.
While the term "botnet" can be used to refer to any group of bots, such as IRC bots, the word is generally used to refer to a collection of compromised machines running programs, usually referred to as worms, Trojan horses, or backdoors, under a common command and control infrastructure.
While the term "botnet" can be used to refer to any group of bots, such as IRC bots, the word is generally used to refer to a collection of compromised machines running programs, usually referred to as worms, Trojan horses, or backdoors, under a common command and control infrastructure.
Labels: anecdote
Friday, February 02, 2007
How to pay less for Windows Vista ?
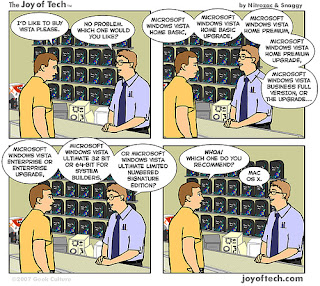 Paul Thurrot explains that on the website Windows IT Pro. Despite the fact that he hasn't tested yet, and then maybe all this stuff is totally wrong, he seems to be well informed.
Paul Thurrot explains that on the website Windows IT Pro. Despite the fact that he hasn't tested yet, and then maybe all this stuff is totally wrong, he seems to be well informed.According to him and Microsoft's internal documents, it would be possible to install Windows Vista from an update DVD, and without having any other OS previously installed. That's about 3 times less expensive.
Here is the procedure. Quite easy:
- Boot with the Windows Vista Upgrade DVD.
- Click "Install Now."
- Do not enter a Product Key When prompted.
- When prompted, select the Vista product edition that you do have.
- Install Vista normally.
- Once the install is complete, restart the DVD-based Setup from within Windows Vista. Perform an in-place upgrade.
- Enter your Product Key when prompted.
Source: Windows IT Pro, this monday.
Labels: computers
archives >> April - March - February - January -December - November - October - September - August - July - June - May
Powered by Stuff-a-Blog
une page au hasard
